Protecting an organization’s cybersecurity can be described as a bifurcated strategy that consists of an external or outside view looking in and internal situational awareness. Organizations face resource challenges including an expertly skilled workforce, availability of current technology tools and services, and limited budgets.
Generally, technology is not the mission of the organization but rather serves as the foundation from which all mission services emanate from. As such, the importance of high-performing technology capabilities and the management of organizational risk through strong technology management cannot be overstated. Too often striking a balance between the degree of IT investment (financial, operational, and administrative) and the correlated impact to organizational operational risk, is a matter of chance rather than design.
A critical internal security strategy centers around the real-time detection of imminent threats or successful exploits. External threat strategies center on managing the network perimeter and controls that impact logical access to an organizations network and computing devices. Understanding how such threats emerge and the role that logical and physical network architecture and management has in managing IT security risk is central to developing and implementing successful countermeasures.
An organizational goal is to reduce risk to an acceptable level. And every organization defines their “acceptable” level of risk differently, largely influenced by the risk-tolerance profile of the organization or their leadership team. Organizations that have been victims of cyber breaches and cyber extortion are more likely to be risk-averse than risk tolerant. Ideally organizations that have not been compromised are increasing their cyber preparedness efforts since cyber threat actors continue to evolve and improve cyber threat tactics.
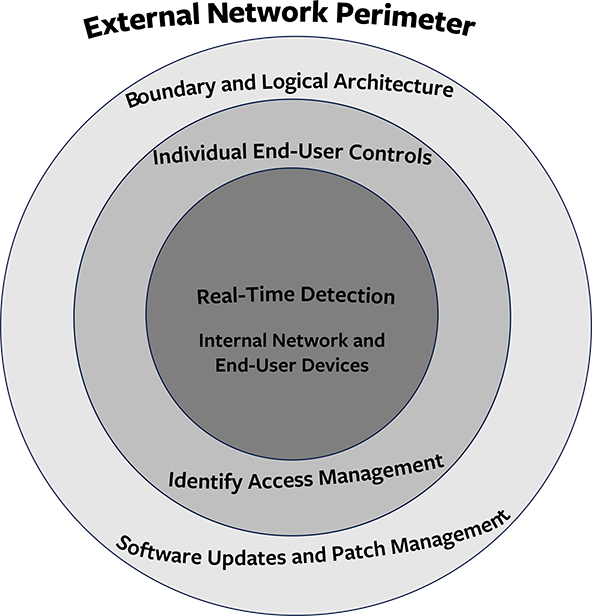
External threat management is primarily achieved through logical network architecture and configuration of perimeter security controls.
- Firewalls and other network boundary controls that manage network traffic in and out of the network are the first line of defense against external threats. Monitoring, managing, and updating version and patch levels and software updates of boundary controls is simple and unsophisticated activity that requires discipline and structured processes to ensure that the tasks are completed in a timely and thorough manner.
- Apply or configure patches and updates for known vulnerabilities. Staying current with vendor alerts, industry news and running routine, if not real-time, vulnerability checks is essential to ensuring this threat vector is adequately managed. There are still frequent news stories of victimized organizations that upon retrospective forensic analysis get attributed to failing to apply or configure patches and updates for known vulnerabilities. Those failures are analogous to a self-inflicted injury.
- Internal threat management encompasses both the physical and logical internal network as well as all corporate network connected devices, whether remote or in-house. Real-time threat detection is a technical countermeasure, usually in the form of host-based intrusion protection on end-user computers and network connected devices. The growth of AI capabilities, in conjunction with traditional software and hardware detection devices, greatly improves the effectiveness of security controls. The growth of threat actor focuses on identifying and quickly exploiting “zero-day” or “day-one” vulnerabilities has accelerated the importance of promptly responding to industry or vendor news about such exploits and available countermeasures. Organizational leaders need to be connected to news sources, both public and private, that will share “Indicators of Compromise” (IOC) alerts and similar news in a timely manner.
One area of critical focus that spans both external and internal security strategy concerns is Identity access management. The stronger the organizational commitment to Identity and access management, the tougher it is for threat actors to breach an organization passively.
Many cyber exploits are carried out via simple end-user exploits, the most common being phishing emails in their many forms. Implementing dual-factor authentication is a very effective countermeasure against most phishing exploits that target harvesting credentials. In addition to being an effective countermeasure, dual-factor authentication also serves to alert the organization of cyber threats through failed log-in attempts by threat actors who have harvested credentials but can’t provide the second-factor credential in the authentication process. These failed attempts are logged and if properly monitored can alert the IT team to suspicious activity.
Conducting periodic access reviews of privileged network access accounts, and privileged users, is also a strong measure for ensuring that access to network resources and applications is limited to the appropriate employees and organizational roles, and that said access is being used appropriately. Routinely auditing access to information systems to ensure that only the right roles and individuals have access, and that the degree of access is appropriate for the role, is a critical activity that serves the dual purpose of ensuring that identity access is appropriate, and that organizational controls are working as intended.
In today’s rapidly evolving digital landscape, organizations must adopt a comprehensive approach to cybersecurity that addresses both external and internal threats. It is paramount that technology not just serves as a foundation, but as a proactive shield, continuously adapting to emerging cyber challenges. By understanding the nuances of threat management, from network perimeter controls to real-time internal detections, organizations can fortify their defenses.
Related articles from The Scope
An Interview with ChatGPT on the State of Texas Health Care
THA sat down with the popular AI chatbot to get…
COVID-19 in Texas Hospitals: Three Years Later
This month marks three years since the COVID-19 pandemic irrevocably…
Homeward Bound Health Care
From infection prevention to telemedicine, the COVID-19 pandemic dramatically changed…
Implementing Sustainable Health Care
Going green, or making efforts to reduce negative environmental impacts…
Protecting your patients, data and infrastructure – battling rising cyber risk
By INSURICA and Cyberforce|Q Health care organizations are one of…
Achieving Supply Chain Stability
With the pandemic waning, one might think that the strain…







